Open Source Firmware
Workshop
building coreboot, run emulations, flash firmware, start hacking
Disclaimer: You'll need to bring your own laptop. If you didn't, get it now.
License
Open Source Firmware Workshop by Patrik Tesarik is licensed under a Creative Commons Attribution 4.0 International License.
These slides & workshop is based on previous work done by:
- Patrick Rudolph
- Christian Walter
- Felix Singer
and would have not been possible without them
Content
Part I
- What's firmware?
- Why should I care?
- coreboot intro
- Hands-On: coreboot in QEMU
Part II
- Flash IC
- Programmers
- Hands-On: Readout firmware from flash IC
- Flash layout
Part III
- Build coreboot for Apollolake
-
Hands-on: Build coreboot for UP²
-
Hands-on: Run coreboot on UP²
Optional:
Start hacking!
- Hacker(wo)man: Build LinuxBoot payload and run it on UP²
Part I
What's firmware?
Firmware: Software that controls hardware

Host processor
firmware
We're going to hack on BIOS firmware

Why should I care?
Vendor firmware:
- propriatary
- buggy
- slow
- legacy technology

Remember:
Firmware controls our hardware
at sub-OS level
coreboot to the rescue

coreboot
open source firmware

- R. Minnich & S. Reinauer @ 1999
- Community project
-
- mail coreboot@coreboot.org
- irc #coreboot
- slack #coreboot-dev
- Active & upstream developement
- QA & CI
coreboot's approach: Plattform initalisation

Bootblock
- Partly written in Assembly, rest is C
- Setup Cache-As-RAM
- Set up Heap/Stack for C Environment
- Decompress and load next stage
- on x86:
- Microcode updates
- Switching from 16bit real mode to
32bit protected mode

Romstage
- Minimal Device Initialization
- GPIO
- UART
- PCI/IO BAR
- Timer init
- DDR DRAM Training (~5secs per DIMM)
- Store DRAM Training Results in MRC Cache
- LZ4 Compressed

Postcar Stage

- Late Cache-As-RAM shutdown
- Only used on Intel devices.
- Console Init
Ramstage

- Memory Handling
- PCI Device Enumeration/Resource Allocation
- Device Init
- Graphics Init
- TPM Init
- CPU Init
- SMM Setup
- ACPI Table Generation
- SMBIOS Table Generation
- Device Tree Patching
- Platform Lockdown
- The biggest stage in coreboot
- Usually, LZMA compressed
Verstage

- Only when verified boot is enabled
- Installs a hook to verify a file/stage before it gets loaded.
- Root-of-Trust
Part I: Hands-On
Hands-on: Build your toolchain
Hands-On: Build your Toolchain
$ git clone --recurse-submodules https://github.com/9elements/coreboot.git $ cd coreboot
20 min
Clone coreboot repository and submodules:
Build the toolchain:
$ make crossgcc-i386 CPUS=`nproc`
Install the following packages:
apt install git make build-essential gnat flex bison libncurses5-dev \ wget zlib1g-dev acpica-tools patch pciutils-dev ccache qemu python \ uuid-dev nasm
dnf install git make gcc-gnat flex bison xz bzip2 gcc g++ ncurses-devel \ wget zlib-devel acpica-tools patch pciutils-devel ccache qemu python \ libuuid-devel nasm
Build System
coreboot
- Same mechanism as in GNU/Linux
- Kconfig
- Defines dependencies
- User-specific configuration in .config file
- Lots of defaults
- Makefile
- Makefile.inc
- Depends in Kconfig choices
- Allows to skip building files
Build System
Build System

Build System

Hands-on
Compile coreboot for QEMU
Hands-On: Compile coreboot for QEMU
20 min
Select payload:
$ make menuconfig
Open the config menu:
$ make nconfig
$ make xconfig
Add a payload --> (None)
Build:
$ make
Run:
$ qemu-system-i386 -M pc -m 1024M -bios build/coreboot.rom -serial stdio
Part II
Flash ICs
How do they look like?

CC-by-SA Raimond Spekking

CC-by-SA Tobias ToMar Maier

CC-by-SA MOS6502
Flash ICs
- Typical SPI / QSPI
- SOIC-8 and WSON-8 common packages
- Easily identified by colored point on the chip
- 3.3V, 2.5V and 1.8V
1980
Today
64KB
512KB
4MB
16MB
512MB
-
Vendor specific
- instructions
- page size
- block size
- #blocks
- software write protection
- erasure time
- OTP
Programmers
- No external components
- Needs Operation System drivers
- Needs "Recovery mechanism"
- Transparent flash IC
- Very fast
- "software based" write-protection might interfere
- "hardware based" write-protection might interfere
internal
external
- Needs external components
- Hardware might interfere
- Voltage / current limits
- Support for flash IC
- Slower
- No recovery needed
- "hardware based" write-protection might interfere
Programmers
internal
external
Baseboard Management Controller
- Only on server platforms
- Recovery mechanism
- Very fast
- High external component count
- Also allows Serial-over-LAN
- Good for debugging and testing
External Programmers
SF100
- https://www.dediprog.com/product/SF100
- SPI programmer
- FullSpeed USB interface
- +160 sec for 16MiB flash

CC-By-SA Patrick Rudolph
External Programmers
SF600
- https://www.dediprog.com/product/SF600
- SPI programmer
- HighSpeed USB interface
- +94 sec for 16MiB flash
CC-By-SA Patrick Rudolph



CC-By-SA Patrick Rudolph
CC-By-SA Patrick Rudolph
External Programmers
for hackers: Raspberry PI
- Native SPI interface
- Ethernet
- Uploads 16MiB in 10 seconds
- GPIOs / UARTs / I2C
- Short circuit might cause the CPU to reboot

CC-By-SA Patrick Rudolph
External Programmers
buspirate and SPI compatible
- Cheap
- Bit bang mode (1 bit per USB transaction)
- Very slow
- Very slow !
- Uploads 16MiB in +30 minutes
External Programmers
wiring


-
Not safe to use external power supply
- Try to use 'S3 resume' or 'WoL'
- Might power the SoC
- SoC might missbehave or read from flash ...
- Make sure voltages are OK
- Safe to apply external power
- Doesn't power SoC
SPI flash IC
SPI flash IC
External Programmers
rules for wiring
- Make sure pinout is correct
- Make sure voltage is correct
- Use a current limited power supply
- Start with low frequencies
- Use short wires
https://doc.coreboot.org/flash_tutorial/index.html
UP²
UP²

- Dual GBE
- 3x USB3.0
- USB OTG
- SATA
- M2/MiniPCI
- Camera
- LCD
- 40 pin connector + FPGA for runtime pin mux
- Intel Apollolake
- 1.1 Ghz Dual Core
- 1 MiB L2 cache
- LPDDR3 / LPDDR4
- Features
- iTPM
- BootGuard
CPU
Board
Hands-on:
Connecting an external programmer
Hands-On: Connecting the external programmer


10min
Hands-On: Connecting the external programmer
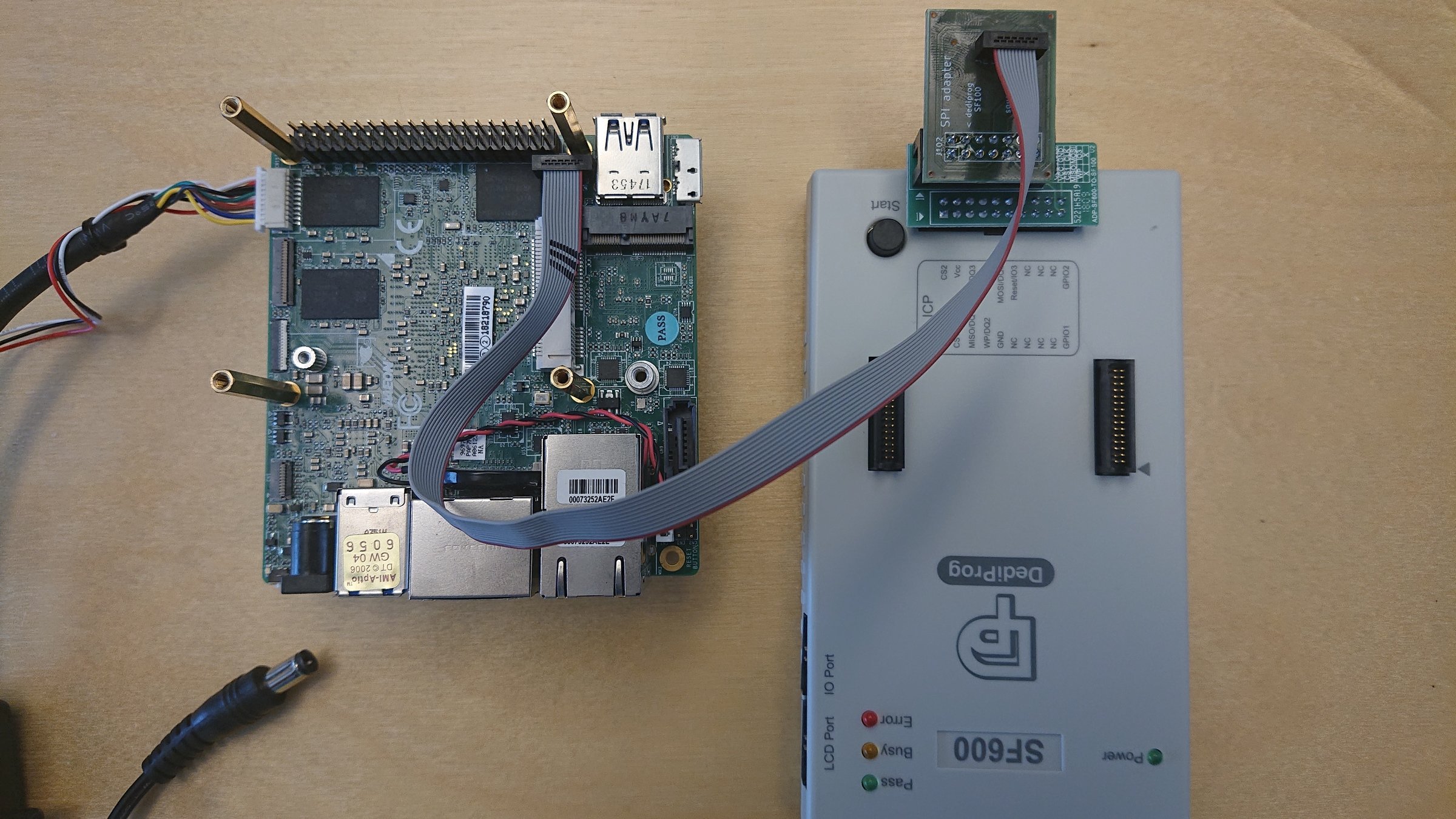
flashrom
general
- flash programmer interface tool
- Developed by Carl-Daniel Hailfinger and Stefan Tauner for a long time
- Core developers:
- David Hendricks @ Facebook
- Nico Huber @SecuNet
- Supports
- 476 flash chips
- 291 chipsets
- 500 mainboards
- 79 PCI devices
- 17 USB devices
- various parallel/serial port-based programmers.
- crossplatform
https://review.coreboot.org/flashrom.git
flashrom
advice reading firmware
- Make sure no other bus master is active
- Make sure not to power the whole board
- Read twice and compare the BLOBs
- Try to lower frequency on transmission errors
- Do not use ATX power supplies
Hands-on: Dumping the vendor firmware
Hands-on: Dumping the vendor firmware
Task:
- Run flashrom
- Run flashrom again
- Binary compare images
What you need:
- UP² board
- External programmer
20min
Hands-on: Dumping the vendor firmware
Reading the flash IC:
$ flashrom -pdediprog:voltage=1.8V -r /tmp/dump1.bin
$ flashrom -pdediprog:voltage=1.8V -r /tmp/dump2.bin $ diff /tmp/dump1.bin /tmp/dump2.bin
Writing the flash IC:
$ flashrom -pdediprog:voltage=1.8V -w /tmp/backup.bin
Hands-on: Dumping the vendor firmware
Verify what you got:
$ cd coreboot/util/ifdtool $ make $ ./ifdtool -d /tmp/dump1.bin
Flash layout
IFD - Intel Flash Descriptor
- Supported since ICH7
- Contains:
- Flash layout
- Access permissions
- Flash special instructions
- OEM section
- Number of flash ICs
- Maximum SPI bus clock
- predefined regions for bus masters
- ...

IFD - Intel Flash Descriptor
but ...
- No support for fine-grained updates
- Vendor specific
- Layout might change in the future
- Not under firmware control
- Starting with Skylake it has 20 regions
Flash layout on UP² vendor firmware

IFWI - Integrated Firmware Image
- IFWI is a filesystem inside the bios region
- Contains the TXE BLOB (usually separate region in IFD)
- Contains the bootblock (usually at end of bios region)
- At end of IFWI the OEM BootBlock partition is placed
- OBB contains coreboot
Flash IC

OBB - OEM Bootblock
- coreboot uses the whole OBB
- APL specific: Last 256KiB aren't usable
- Unused bootblock at end of COREBOOT(CBFS)
Flash IC

Flash layout
Warning
Vendor firmware uses two LBP, but coreboot uses one LBP
We have to patch IFD to support one LBP!
Part III
Build coreboot for Apollolake
- You need Intel FSP 2.0
- https://github.com/IntelFsp/FSP
- Redistributable since 23th Aug 2018
- Integrated into coreboot build system
- Configuration values (UPD) are configured at runtime
- Can be split into 3 parts:
- FSP-T
- FSP-M
- FSP-S
- You need microcode updates
- Intel changed the license a few times
- Redistributable since 23rd Aug 2018 (again)
- The format changed from binary to the header in the past
- Documentation on all sites could be improved
- Without Microcode updates, nothing works!!!
Build coreboot for Apollolake
- You need IFWI (BPDT partion)
- Extract from vendor firmware
- You need the IFD
- Extract from vendor firmware
Build coreboot for Apollolake
Hands-on: Build coreboot for UP²
Hands-on: Build coreboot for UP²
Task:
- Select mainboard UP > squared
- Set path to FMAP
- Select
- Use Intel Firmware Support Package
- Add Intel descriptor.bin file
What you need:
- BLOBs
- Intel IFWI
- Intel IFD
- Microcode BLOBs
- FSP 2.0
30min
Task:
- Build ./util/ifdtool/
- Extract IFD regions using ifdtool
- Generate a layout file using ifdtool
What you need:
- coreboot ifdtool
- UP² board firmware dump
10 min
Hands-on: Extracting the BIOS region
Hands-on: Extracting the BIOS region
$ util/ifdtool/ifdtool -x backup.bin
Extract regions from flash dump using the IFD:
$ make -C util/ifdtool
Build ifdtool:
Hands-on: Build coreboot for UP²
Place BLOBs at:
$ mkdir -p 3rdparty/blobs/mainboard/up/squared/
Create a folder whithin coreboot:
-
3rdparty/blobs/mainboard/up/squared/ifwi.bin
-
3rdparty/blobs/mainboard/up/squared/descriptor.bin
Patch IFD at offset 0x1ff and set bit3!
Hands-on: Build coreboot for UP²
- Select mainboard UP > squared
- Set path to FMAP: src/mainboard/$(CONFIG_MAINBOARD_DIR)/upsquared.fmd
Set the following path in menuconfig:
- Select Chipset
- [*] Write content into IFWI region
- Set path to 3rdparty/blobs/mainboard/$(CONFIG_MAINBOARD_DIR)/ifwi.bin
- [*] Add Intel descriptor.bin file
- Set path to 3rdparty/blobs/mainboard/$(MAINBOARDDIR)/descriptor.bin
- Select Console
- [*] Enable early (bootblock) console output
- [*] Serial port console output
$ make
Hands-on: Build coreboot for UP²
fallback/postcar 0xb6800 stage 18272 none
fallback/dsdt.aml 0xbafc0 raw 5581 none
img/coreinfo 0xbc600 simple elf 50932 none
fallback/payload 0xc8d40 simple elf 67438 none
payload_revision 0xd9500 raw 235 none
(empty) 0xd9640 null 11125080 none
bootblock 0xb757c0 bootblock 32768 none
Built up/squared (Squared)
Image written successfully to build/cbfs/fallback/ifwi.bin.tmp.
Image does not contain sub-partition OBBP(6).
Sub-partition IBBP(4) entry IBBL replaced from file build/cbfs/fallback/bootblock.bin.
Image written successfully to build/cbfs/fallback/ifwi.bin.tmp.
W: Written area will abut bottom of target region: any unused space will keep its current contents
Final output:
coreboot rom is placed:
./build/coreboot.rom
Hands-On: Connect the UART
Hands-on: Connect
the UART

2min

CC 4.0
CC 4.0
Hands-on: Run coreboot on UP²
Hands-on: Run coreboot on UP²
Task:
What you need:
- coreboot.rom build for UP²
- an external programmer
- a 3.3V TTL serial adapter
- Flash the coreboot.rom
- Attach to the serial
- Power the UP²
- Watch the serial console
15min
Hands-on: Run coreboot on UP²
Flashing coreboot on UP²:
$ flashrom -pdediprog:voltage=1.8 --fmap -i COREBOOT -w build/coreboot.rom
Flashing update IFD on UP²:
$ flashrom -pdediprog:voltage=1.8 --ifd -i ifd -w build/coreboot.rom
Optional: Hacking
LinuxBoot
- The idea of running Linux inside the firmware
- Well tested drivers for anything
- Graphics
- USB
- Input device
- Block devices
- SCSI devices
- Network
- EC/SuperIO
- Easy to write application programs
- You don't need firmware engineers
- Project works with coreboot, UEFI and u-boot
- If you are stuck with non-coreboot OCP HW look into the repository for LinuxBoot UEFI supported boards.
- coreboot integration
- Graphics output via KMS and VBT
- Requires external toolchain (non x86)
- EFI boot support
- GRUB2 config support
- Big payload size
- Bigger attack surfaces
- Drivers for VPD, CBMEM console and coreboot framebuffer are available
linuxboot.org
u-root
- Golang initramfs generator
- Only 4 go binaries
- Has an init system and can start systemd
- Supports source/bb build mode
- Compiles everything into a initramfs.cpio
- Supports libraries aka pkg/*
- Is a coreutils replacement and tools can be found under cmds/*
- Tooling is currently somehow complicated because the use of flags
- Missing Golang kexec implementation for other than x86 but kexecbin is available
u-root.tk
Hands-on:
Build coreboot + LinuxBoot
Hands-on: Build LinuxBoot
Task:
- Select LinuxBoot as payload
- Compile a kernel and u-root
- Build coreboot
What you need:
- coreboot firmware for the UP²
- A Go 1.9+ toolchain
- A GNU-Linux toolchain
45min
Hands-on: Build LinuxBoot
- Install a Go 1.9+ toolchain
- Install a GNU-Linux toolchain
Note: The coreboot toolchain isn't used for Linux paylods


Hacking required:
Linux Kernel gets build with '-fstack-protector' in host toolchain.
This breaks booting the target kernel while loading x86/purgatory.
"Fix":
Disable stack-protection in Kconfig
Run:
$ cd payloads/external/Linuxboot/linuxboot/kernel-*
$ make menuconfig
Architecture-dependend options >
[ ] Stack Protector Buffer overflow protection
Run:
cd $your_coreboot_dir
make CPUS=$(nproc)
Hands-on: Build LinuxBoot

Additional Info:
Flash Map
Hands-on: Creating a layout file
$ util/ifdtool/ifdtool -f layout backup.bin
Extract the layout from IFD:
Use the layout in flashrom:
$ flashrom -pdediprog:voltage=1.8 -w backup.bin -l layout -i bios
Starting with flashrom 1.0:
$ flashrom -pdediprog:voltage=1.8 -w backup.bin --ifd -i bios
FMAP - Flashmap
- Developed by google in 2015
- Vendor independent flash layout
- Each region has multiple subregions
- Converted by fmaptool
- Can be referenced in coreboot
- Build time sanity checks
- Patches for flashrom pending
FMAP - Flashmap
$ cat /src/mainboard/up/squared/upsquared.fmd
FLASH 16M {
SI_DESC@0x0 0x1000
SI_BIOS@0x1000 0xefe000 {
IFWI@0x0 0x2ff000
OBB@0x2ff000 0xbff000 {
FMAP@0x0 0x800
UNIFIED_MRC_CACHE@0x800 0x21000 {
RECOVERY_MRC_CACHE@0x0 0x10000
RW_MRC_CACHE@0x10000 0x10000
RW_VAR_MRC_CACHE@0x20000 0x1000
}
CONSOLE@0x21800 0x20000
COREBOOT(CBFS)@0x41800 0xb7d800
BIOS_UNUSABLE@0xbbf000 0x40000
}
}
SI_DEVICEEXT@0xeff000 0x101000 {
DEVICE_EXTENSION@0x0 0x100000
UNUSED_HOLE@0x100000 0x1000
}
}
IFD vs FMAP
Flashing a single FMAP region
- flashrom version 1.1 adds the --fmap option
- allows to flash a single FMAP region
$ flashrom --fmap -i RW_SECTION_B -w coreboot.rom
Build coreboot for Apollolake
- You need BLOBs
- Some are not redistributable
- VGA Options ROMs
- Intel ME/Intel TXE
- IFWI
- Some are platform specific
- GBE
- Intel IFD
- You can dump them from your hardware
-
Use flashrom -r backup.rom to read the full image
-
Use ifdtool -x backup.rom to extract Intel IFD and Intel ME
-
-
Copy BLOBs to 3rdparty/blobs
-
Integrate them into the build
- Some are not redistributable
BLOBs

- Intel IFD
- GBE
- Intel ME/Intel TXT
- BIOS
- VGA Options ROMs
- IFWI
- uCode
- FSP1.0/ 2.0
Where to find blobs:
FSP 1.0

FSP 2.0
